As we move deeper into 2024, cyber attacks continue to evolve, becoming more sophisticated and potentially damaging. But don’t worry—understanding these threats is the first step toward protecting your business. Whether you’re a seasoned IT pro or a small business owner trying to keep up, we’re here to guide you through the most common types of cyber attacks in 2024. Let’s break them down so you can confidently take steps to safeguard your company.
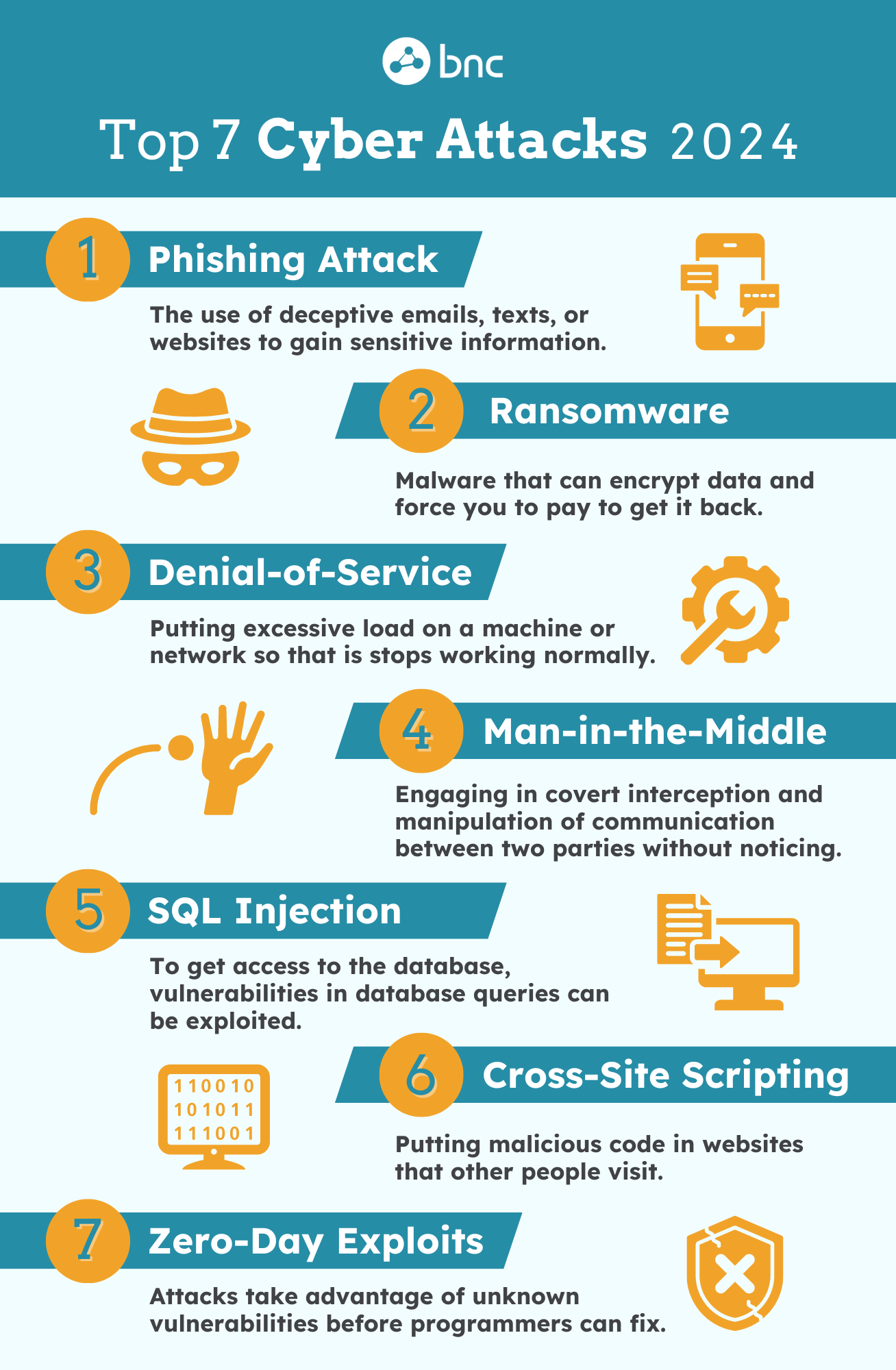
1. Phishing Attacks
You’ve probably encountered phishing before. It’s the classic scam: a hacker sends an email, maybe pretending to be your bank or a trusted partner, tricking you into giving up sensitive information. Phishing is everywhere because it works. But with a little awareness, you can avoid falling into the trap.
How to defend yourself: Keep an eye out for suspicious emails, educate your team to recognize phishing attempts, and add an extra layer of protection with multi-factor authentication (MFA).
2. Ransomware
Ransomware is like the cyber version of a hostage situation. Hackers lock down your data, and they won’t give it back unless you pay a ransom. What’s worse is the rise of double extortion—where hackers not only encrypt your data but also threaten to leak it if you don’t pay up. This can be catastrophic for any business.
How to defend yourself: Regularly back up your data, invest in advanced security tools, and always keep your software up to date. Prevention is your best defense.
3. Denial of Service (DoS) and Distributed Denial of Service (DDoS) Attacks
Imagine a crowd of people rushing into your store all at once, overwhelming your staff so much that you can’t serve anyone. That’s what a DoS or DDoS attack does to your website or service—bombards it with so much traffic that it crashes. This can lead to downtime and lost revenue, which nobody wants.
How to defend yourself: Use a DDoS protection service, set up traffic filtering, and ensure your web host has strong defenses in place.
4. Man-in-the-Middle (MitM) Attacks
In a MitM attack, the hacker is like a spy eavesdropping on your conversations—intercepting communication between two parties. This can happen on public Wi-Fi networks, making it all too easy for them to steal login details or other sensitive data.
How to defend yourself: Always use secure connections (look for HTTPS in the browser), enable VPNs for remote work, and avoid public Wi-Fi for anything sensitive.
5. SQL Injection
If you have a website, SQL injection is a risk. Attackers insert malicious code into your web forms, and suddenly they can access, change, or delete your data. This can be a nightmare for anyone running a website that relies on databases.
How to defend yourself: Always sanitize user inputs, limit database permissions, and regularly update your web software to patch vulnerabilities.
6. Cross-Site Scripting (XSS)
With XSS, hackers inject malicious scripts into web pages that others view. If someone visits the compromised page, the script runs in their browser without their knowledge. This can lead to stolen information or worse.
How to defend yourself: Practice secure coding, sanitize all inputs, and use tools like content security policies (CSPs) to block unauthorized scripts.
7. Zero-Day Exploits
A zero-day exploit is the nightmare scenario where a hacker finds a vulnerability before the software vendor even knows about it. Since there’s no patch available, zero-day exploits are particularly dangerous.
How to defend yourself: Keep all your software up to date, monitor for unusual activity with endpoint protection, and invest in threat detection tools that can identify these kinds of attacks early.
Why These Attacks Matter for SMBs
If you’re running a small to medium-sized business, you might be thinking, “Will these cyber attacks really happen to me?” The truth is, many SMBs are prime targets because attackers assume they have weaker defenses. These attacks can cause huge disruptions, financial loss, and damage to your reputation.
Fortunately, you can take action today. Basic cybersecurity hygiene, like regular data backups, employee training, and staying on top of software updates, can make a world of difference. And if it all feels a bit overwhelming, don’t hesitate to reach out to a trusted partner—like BNC—who can help you stay a step ahead of cybercriminals.
Creating a Cyber-Savvy Business
One of the most important things you can do is build a security-conscious culture in your business. That means regular training for employees, setting up multi-factor authentication, and ensuring that no one is reusing passwords. The goal is to make cybersecurity part of everyday operations.
Get In Touch With BNC To Get Started
 The world of cyber attacks is always changing, but staying informed and proactive can help your business thrive without the worry of falling victim. Phishing, ransomware, and zero-day exploits might sound scary, but by understanding these threats and taking action, you can significantly reduce your risk. Contact us today for a free consultation! Your company may be on the lookout for more comprehensive IT solutions than just secure browsing, and we’re here to help. If you’re looking for an IT company in Denver or Dallas with experienced IT/Security consultants, BNC will work closely with your team to evaluate your specific needs and provide tailored solutions that strengthen your cybersecurity defenses. Don’t wait until a cyber incident occurs to realize the importance of comprehensive cybersecurity measures. Contact BNC, a managed IT services provider in Dallas & Denver today to begin your journey toward a safer and more secure digital future. Together, we can safeguard your business and protect it from the ever-present threats in the world of cybercrime.
The world of cyber attacks is always changing, but staying informed and proactive can help your business thrive without the worry of falling victim. Phishing, ransomware, and zero-day exploits might sound scary, but by understanding these threats and taking action, you can significantly reduce your risk. Contact us today for a free consultation! Your company may be on the lookout for more comprehensive IT solutions than just secure browsing, and we’re here to help. If you’re looking for an IT company in Denver or Dallas with experienced IT/Security consultants, BNC will work closely with your team to evaluate your specific needs and provide tailored solutions that strengthen your cybersecurity defenses. Don’t wait until a cyber incident occurs to realize the importance of comprehensive cybersecurity measures. Contact BNC, a managed IT services provider in Dallas & Denver today to begin your journey toward a safer and more secure digital future. Together, we can safeguard your business and protect it from the ever-present threats in the world of cybercrime.
Need help? Let BNC be your guide. We’re here to help you build a resilient, secure IT environment so you can focus on what matters—growing your business.
