SMBs are facing a growing number of cybersecurity challenges as hackers sift through the internet to find victims to exploit. Among these, social engineering attacks stand out due to their ability to exploit human weakness, and it’s often not a kind of attack that people outside of IT would think happen, but they do. Understanding and mitigating these threats is crucial for SMBs to safeguard their operations, data, and reputation, which are all at risk when they approach this vulnerability in a careless way. This blog post delves into the nature of social engineering attacks and offers practical strategies for SMBs to prevent them.
The Human Factor: An Ever-Present Vulnerability
Human error remains one of the most significant vulnerabilities in any organization, regardless of size. Cybercriminals often target employees with sophisticated scams, such as smishing (SMS phishing) and robocall attacks. In today’s remote and hybrid work environments, the widespread adoption of Bring Your Own Device (BYOD) policies introduces additional risks. While BYOD can enhance productivity and reduce costs, it also increases exposure to cyber threats.
The Rising Sophistication of Social Engineering
Social engineering attacks have become increasingly sophisticated, leveraging technologies like artificial intelligence (AI) and deep fakes to create convincing impersonations. Even experienced users can fall prey to these schemes. Attackers often exploit the weakest link in an organization, which is frequently the human element. Disgruntled employees, lost personal devices, and executives deceived by familiar voices or emails are common targets. Phishing (email/messaging), vishing (phone/voice), and smishing attacks are popular methods used by threat actors to gain access to sensitive information.
Case Studies: Real-World Examples
Recent incidents highlight the devastating impact of social engineering attacks:
- Global Ride-Sharing Company: In late 2022, an attacker compromised a contractor’s personal device, purchased the contractor’s corporate password on the dark web, and gained network access after bypassing multifactor authentication (MFA).
- Major Media Company: Hackers impersonated an employee and convinced the IT help desk to provide credentials, leading to a 10-day shutdown of the company’s computer systems.
These examples underscore that if large corporations with extensive resources can be compromised, SMBs are at even greater risk.
The Cost of Personal Device Usage
Employees often use personal devices for work, which can lead to significant cybersecurity risks. This inclination to simplify tasks can result in regulatory compliance failures and financial liabilities. High-profile cases in the financial services industry have demonstrated the costly consequences of improper monitoring of employee communications on personal devices. In 2021, several large financial services providers were heavily fined for failing to maintain proper records of off-channel communications.
Addressing Low-Hanging Fruit: People and Their Devices
Social engineering attacks often target employees and executives, as well as customers and third-party suppliers. Common tactics include:
- Spear Phishing: Targeting specific individuals with personalized attacks.
- Whaling: Focusing on high-level employees.
- Smishing and Vishing: Using text messages and phone calls to deceive victims.
The Verizon 2023 Data Breach Investigations Report (DBIR) reveals that 74% of breaches involve human elements, such as errors, misuse of privileges, stolen credentials, or social engineering.
Vulnerable Technologies
Personal devices used for work tasks pose significant risks, especially when employees use them for both professional and personal activities. Remote work has increased the reliance on these devices, making it crucial for SMBs to manage and secure them effectively. Verizon’s Mobile Security Index (MSI) reports that over 50% of personal devices fell prey to mobile phishing attacks in 2022, highlighting the need for robust security measures.
Is BYOD Worth the Risk?
While BYOD policies can improve productivity and reduce IT costs, they also introduce substantial cyber risks. Personal devices may be rooted, jailbroken, or infected with malware without the user’s knowledge. SMBs must carefully assess the risks and benefits of BYOD policies and consider alternatives, such as corporate-issued devices, to maintain control and visibility over their security posture.
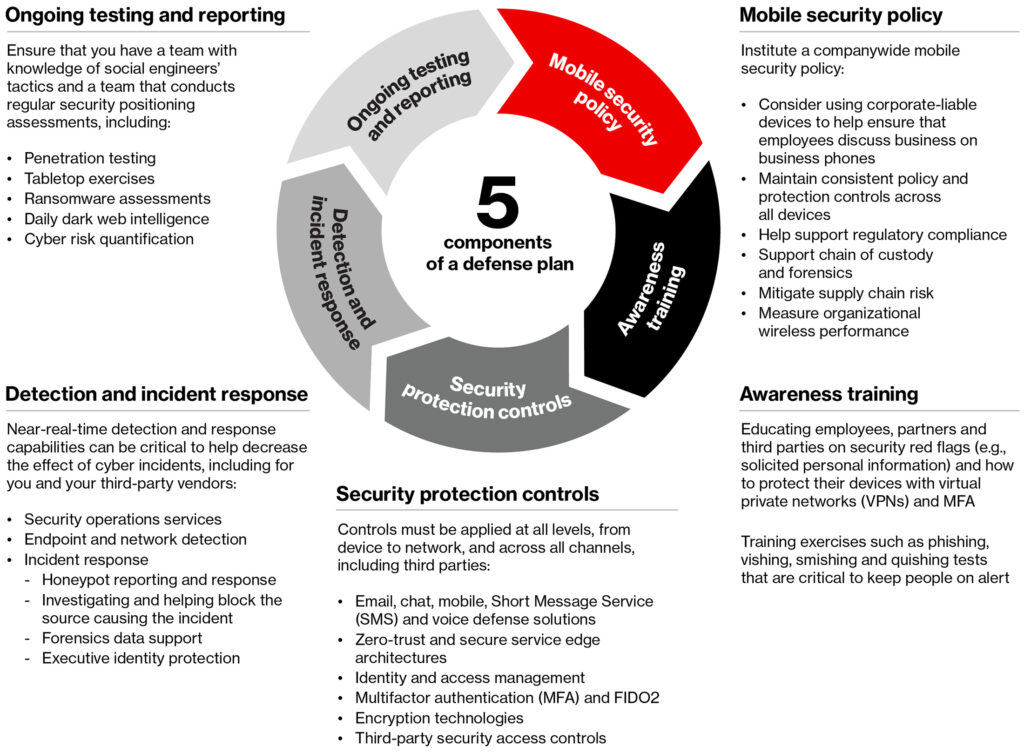
Implementing a Comprehensive Defense Plan
To defend against social engineering attacks, SMBs should focus on two main functions: threat detection and trust enforcement. These functions involve:
- Threat Detection: Identifying and responding to cyber threats, such as unauthorized access and malware.
- Trust Enforcement: Proactively managing identity, passwords, encryption, and access control.
A robust defense plan should include awareness training, mobile security policies, security protection controls, detection and response mechanisms, and continuous monitoring and testing across all devices, applications, and networks.
5 Components of a Social Engineering Defense Plan – Verizon
Human weakness is a significant cybersecurity challenge for SMBs. By understanding the nature of social engineering attacks and implementing comprehensive defense strategies, SMBs can mitigate risks and protect their operations. Prioritizing employee training, enforcing robust policies, leveraging technological solutions, and conducting regular risk assessments are essential steps in building a resilient cybersecurity posture.
Get In Touch With BNC To Get Started
 Your company may be on the lookout for more comprehensive IT solutions than just secure browsing, and we’re here to help. If you’re looking for an managed service provider in Dallas or Denver with experienced IT/Security consultants, BNC will work closely with your team to evaluate your specific needs and provide tailored solutions that strengthen your cybersecurity defenses. Don’t wait until a cyber incident occurs to realize the importance of comprehensive cybersecurity measures. Contact BNC, a managed IT services provider in Dallas & Denver today to begin your journey toward a safer and more secure digital future. Together, we can safeguard your business and protect it from the ever-present threats in the world of cybercrime.
Your company may be on the lookout for more comprehensive IT solutions than just secure browsing, and we’re here to help. If you’re looking for an managed service provider in Dallas or Denver with experienced IT/Security consultants, BNC will work closely with your team to evaluate your specific needs and provide tailored solutions that strengthen your cybersecurity defenses. Don’t wait until a cyber incident occurs to realize the importance of comprehensive cybersecurity measures. Contact BNC, a managed IT services provider in Dallas & Denver today to begin your journey toward a safer and more secure digital future. Together, we can safeguard your business and protect it from the ever-present threats in the world of cybercrime.
Reference: The rise of social engineering and the cost of personal devices: A security perspective